Security Alert
We have experienced a very unique situation where using a Remote Desktop session to connect to a remote system that’s been infected with crypto malware can potentially encrypt files on the originators network.
We recommend that you have the “drives” option disabled on ALL RD session connections.
Without this setting disabled, the remote system can gain access to your mapped redirected drives, and will begin to encrypt the files on them. TURN OFF DRIVE MAPPING as a default setting for all RDC connections.
It’s simple to do, just follow these steps
From the “Local Resources” tab in your RD Connection window, click the “more” button.
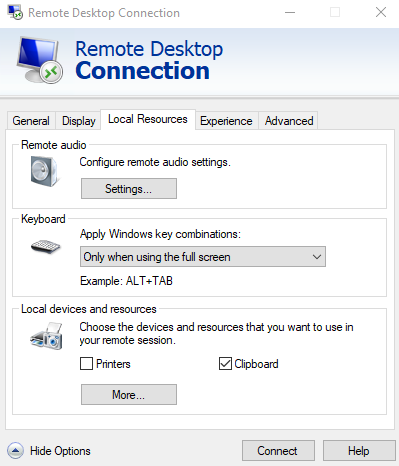
Be sure to UNCHECK the “drives” option in the “Local Drives and Resources” window.
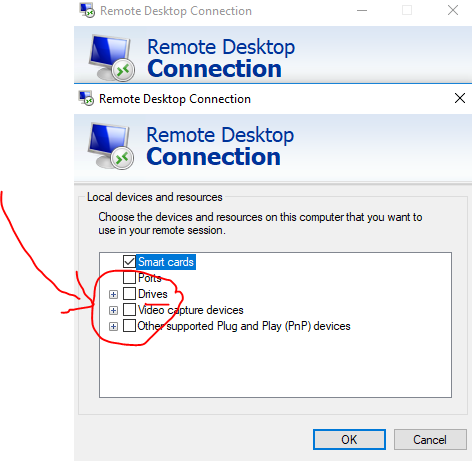
Make this change on all existing RDP connections, or save it to a file and use as your default RDC session connection.



